Systems administrators and network engineers need to configure and monitor a range of logs to keep themselves updated on the status of their Windows networks. They spend hours gleaning event log, security log, application log and various others to ensure that an error does not multiply to unmanageable proportions crippling their networks.
Windows Management Instrumentation (WMI) has long been used to gather information about systems in Windows networks. WMI along with Group Policy Objects (GPOs) have been the staple tracking measures used by network engineers to identify and troubleshoot problems. These along with Remote Registry are all that’s needed most of the time to help administrators monitor their Windows network.
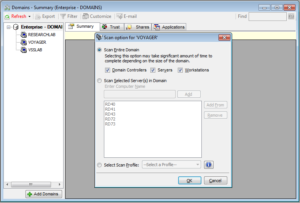
While these provide details about the network adapters used, the hardware and software configuration detail, IP addresses, memory utilized, service packs installed, version of updates applied, roles assigned and policies applied, often administrators need to go beyond these measures and be able to gather domain level data to be able to comply with the reporting and security policies compliance requirements outlined under Sarbanes-Oxley Act (SOX) and the Health Insurance Portability and Accountability Act (HIPAA).
Hence to ensure security, systems administrators and network engineers need to be able to squeeze out every ounce of information they can using the WMI along with GPOs wherever needed and plug all the holes that leave their networks and domains vulnerable to data pilfering and improve reliability.
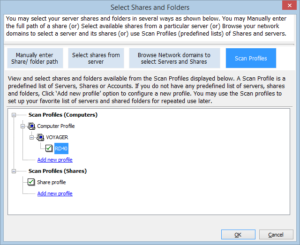
Vyapin Software Systems created network monitoring and security configuration reporting tool that helps administrators to pull out important details that contribute towards improving the efficiency of their networks as also improving the security of the servers and systems that are the lifeline of their networks.
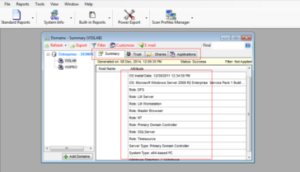
These provide you details like network configuration settings, security hot fixes and updates applied, roles assigned, applications running and their configuration details, etc. To strengthen security, administrators are provided reports about users and groups – domain memberships and privileges, their status, the number of logon attempts successful as well as failed and the resources accessed by them.
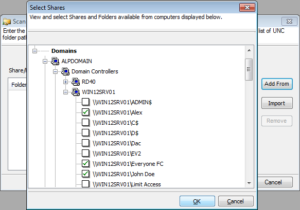
To provide a larger overview of their networks, administrators are also provided details like domain security summary, NTFS permissions across the file servers that are part of their domain, the local and advanced security policies active, as well as details listed in the various logs under Component Services.