As part of managing security and compliance in your IT environment, it is vital to audit and track all the changes happening in AD user accounts. There are a few important changes in user accounts you must consider auditing all AD events related to user accounts to identify and prevent potential security threats. Some of these events are new user accounts created, user accounts deleted, user accounts enabled / disabled, user accounts permissions changes, etc. By constantly monitoring changes (some of which may be unauthorized or by oversight) made to user accounts in Active Directory, you can overcome potential AD security breaches in the future.
Here we have discussed about how to audit user account changes in AD using native Active Directory auditing tool and with Vyapin Active Directory Change Tracker.
Using Native Active Directory Auditing Tool
First enable “User Account Management” audit policy using the steps mentioned below.
- Go to “Administrative Tools”
- From primary “Domain Controller”, open “Group Policy Management” console
- Create a new GPO or edit an existing GPO. Creating a new GPO, link it to domain and edit is recommended.
- From left panel, create a new GPO by right-clicking on the domain name.
- Click “Create a GPO in this domain, and Link it here”.
- On “New GPO” window shown on the screen, give a name (Say: Manage User Accounts) and click “OK”.
- Right-click on the new GPO which appears in left pane click “Edit” in the context menu.
- It will show “Group Policy Management Editor” on the screen.
- Go to “Computer Configuration” ➔ “Windows Settings” ➔ “Security Settings” ➔ “Advanced Audit Policy Configuration” ➔ “Audit Policies” to set “Audit User Account Management” policy.
- Choose “Account Management” policy which will display all its sub-policies.
- Double-click “Audit User Account Management”’ policy to open its “Properties” window.
Note: Configuring above policy in “Advanced Audit Policy Configuration” rather than “Local Policy” because the need of enabling all account management policies in “Local Policy” will create huge amount of event logs.
- In policy properties, select “Define these policy settings” checkbox. As per your auditing attempt requirements, choose any one or both the options (success & failure).
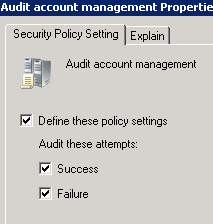
- Click “Apply”, and “OK” to close the properties window.
- Straightway update the Group Policy to reflect the new changes on the entire domain
- Run the following command in the “Command Prompt”:
Gpupdate /force

Once “User Account Management” audit policy is enabled, you can track all the user account changes in AD through event viewer. We have explained how to audit AD user account changes via event viewer.
Monitoring user account changes in AD using Event Viewer
To track Active Directory user account changes,
- Open “Windows Event Viewer”
- Go to “Windows Logs” ➔ “Security”
- In the right pane, click “Filter Current Log” option to list the relevant events
Given below are few events related to user account management:
- Event ID 3452: A user account was created.
- Event ID 3456: A user account was deleted.
- Event ID 3461: A user account was enabled.
- Event ID 3466: A user account was disabled.
- Event ID 3468: A user account was changed.
- Event ID 3471: The name of an account was changed.
- Event ID 3475: A user account was locked out.
Using Vyapin Active Directory Change Tracker
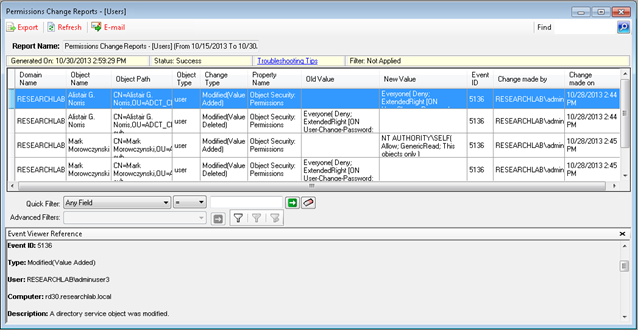
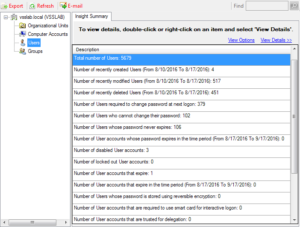
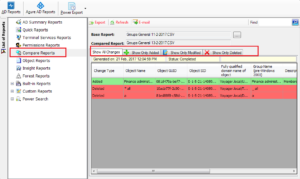
Events Reports in ADChangeTracker is a powerful feature that enables the user to report the events data for AD object changes, User logon/logoff activities, Password change activities and Terminal Services activities based on specific event ID(s) in the security event log of domain controller. You can view events data by specifying the timestamp, domain, change type, category and field based filter query that occurred over a time period.
Benefits
- Reports User Logon/Logoff activities in a domain with valuable information like Client Name, Logon Type and Workstation Name.
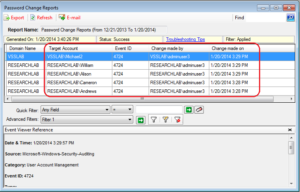
- Reports events data with When and Who made the changes for Password change activities in Active Directory.
- Reports Terminal Services Activities of roaming users in a domain with valuable information like Connected User Name, Workstation Name and Session Type.
- Reports What exactly changed, along with Old Value and New Value, When the change was made, Where the change was made in Active Directory and Who made the changes in Active Directory objects.
Try Vyapin Active Directory Change Tracking Tool Now!