This primer is intended to introduce the reader to NTFS file system in Windows. Even though the NTFS file system is more than 2 decades old, it is still one of the less understood. This article gives a quick introduction to NTFS, covering the most essential elements which may be further explored using various articles in Microsoft’s TechNet and MSDN.
NTFS is the standard file system of Windows NT and all Windows operating systems that are available to drives formatted with NTFS. Windows operating systems introduced changes that included control over NTFS permissions and how permissions are configured to share folders and files. You use shared folders to provide Local/Network users with access to resources. The advantage of NTFS permissions is that they affect local users as well as domain users based on the permissions granted to each individual user during Windows logon.
What is NTFS Permissions?
In a Windows Network, you can set sharing permissions on shared folder and files. Each user can have access to entire folders or individual folders within the Network. Administrators can use the NTFS Permissions to provide access control to folders, files, containers and objects on the network using what is known as the “Security Descriptor”. This security descriptor describes what kind of access is allowed for individual users and groups of users and allows users and administrators to control security on their files and folders.
Each permission assigned to a user or group is added to the system by what is known as an Access Control Entry (ACE). The entire set of permissions entries in a security descriptor is known as a permission set or Access Control List (ACL). It is this ACL that governs all accesses to folders and files in NTFS file system.
Explicit vs inherited permissions
There are two types of permissions set on objects: Explicit permissions and Inherited permissions.
Explicit permissions are those that are set by default on non-child objects when the object is created, or by user action on non-child, parent, or child objects.
Inherited permissions are those that are propagated to an object from a parent object. Inherited permissions ease the task of managing permissions and ensure consistency of permissions among all objects within a given container.
Allow vs Deny permissions
While assigning the permissions to users or groups, you need to specify whether the entry should have access (Allow) or not have access (Deny) to a shared folder or file. Deny permissions always take precedence over any other Allow permissions.
Understanding Folders and Files Permissions
On NTFS volumes, you can set NTFS Security Permissions to folders and files. These permissions allow or deny access to the folders and files. There are two different views of permissions as given below,
1. Basic or Standard Permissions:
The basic permissions you can assign to folders and files, that includes Full Control, Modify, Read & Execute, Read, and Write. Basic NTFS Permissions explained briefly as below,
- Full Control: Users can have full access rights to add, modify, delete to files and directories. Additionally, user can change permissions settings for all files and sub-directories.
- Modify: Users can have only access to view and modify files and their properties, including deleting and adding files to a directory.
- Read & Execute: Users can have access to execute files, including scripts.
- Read: Users can have only access to view files and folders.
- Write: Users can have access to modify the files inside of directories.
2. Special or Advanced Permissions:
The basic permissions are created by combining special permissions of special groups. Using advanced permissions settings, you can assign the special permissions individually
- Full control: Users can have full access rights to add, modify, delete to files and directories. Additionally, user can change permissions settings for all files and sub-directories.
- Traverse folder / execute file: Users allows that you can allow or deny moving from folders to others files or sub-folders even if they have no permissions for the traversed files or folders.
- List folder/ read data: Users can view the name of files and sub-folders within the folders. List folders affects the contents of that folder and do not affect folder are setting the permissions. Read data is for viewing the data in files.
- Read attributes: Users can view the attributes of a file or folder such as read only and hidden attributes are define by NTFS.
- Read extended attributes: User can view the extended attributes of a file or folders.
- Create files / write data: This Create files permissions (only applies to folders) allows user to create a files within the folder. The Write data permissions (only applies to files) allows user to overwrite the existing content of a file.
- Create folders / append data: This Create folder permissions (only applies to folders) allows user to create folder within a folder. The Append data (only applies to files) allows user to changes to the end of the file, but not allow to change, delete or overwrite existing data.
- Write attributes: Users can write the attributes of file or folder such as read-only or hidden attributes are defined by NTFS. This permissions does not imply to create or delete files or folders.
- Write extended attributes: Users can change the extended attributes of a file or folder such as read-only or hidden are defined by NTFS.
- Delete: Users can delete the file or folder. (If users don’t have the Delete permissions on a folder or file, they can still delete it if they have the Delete Subfolders and files permission on the parent folder.)
- Read permissions: Users allows you to read permissions of the file or folder such as Full Control, Read, and Write etc..,
- Change permissions: Users allow you to change an existing permissions of the file or folder.
- Take ownership: Users can take ownership of a file or folder. The owner of a folder or file can always alter the permissions on it, regardless of any existing permissions that protect the file or folder.
How to view / modify NTFS permissions?
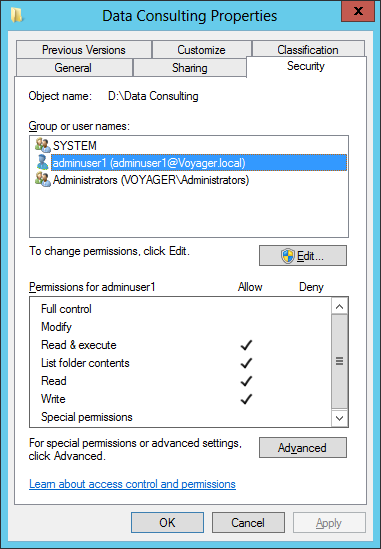
The most common way to check or view the NTFS permissions is to use the Windows Explorer. To view or modify NTFS Permissions for an object
- In Windows Explorer, right click a folder, file and select “Properties” from the context menu. The properties dialog box appears.
- Click the Security tab. It shows name of the users/groups that are assigned to the folder or file under Group or user names.
- Select group or user for which you want to view the Allow and Deny permissions. Also, to view special permissions, click Advanced
- Change the settings, if desired, and click OK or Apply to save your changes.
How to Set / Remove NTFS Permissions?
- Right-click a folder, file and select “Properties” from the context menu. The properties dialog box appears.
- Click the Security tab. It shows name of the users/groups that are assigned to the folder or file under Group or user names.
- Click “Edit” option, The Permissions for an object (Selected Folder or File) dialog appears as shown below,
- To Add a new account, Click “Add” button option with a desired NTFS Permissions.
- To Remove an account, Select group or user under a list of “Group or user names” and Click “Remove” button option.
How to Copy NTFS Permission from one folder to another folder?
You can Copy NTFS Permissions from one folder to another folder by using Windows PowerShell steps as given below,
- Click Start, and then click Windows PowerShell with elevated (Run as Administrator) privileges.
- Type the below cmdlets, to copy NTFS Permissions from source folder to destination folder or file.
Get-Acl -Path “Source file or folder path” | Set-Acl -Path “Destination file or folder path”
How to Backup NTFS Permissions?
You can Backup NTFS Permissions by using Windows PowerShell cmdlets, following steps as given below,
- Click Start, and then click Windows PowerShell with elevated (Run as Administrator) privileges.
- Type the below cmdlets, to Backup NTFS Permissions for folder or file.
Get-Acl -Path “file or folder path” | Select-Object Path, Sddl | Export-Csv “Output File”
E.g: “Output File” -> “D:\Export\Export.csv”
How to Restore NTFS Permissions?
You can Restore NTFS Permissions by using Windows PowerShell cmdlets, following steps as given below,
- Click Start, and then click Windows PowerShell with elevated (Run as Administrator) privileges.
- Type the below cmdlets, to restore NTFS Permissions from the exported file.
Import-Csv “OutputFile” | ForEach-Object
{
$acl = Get-Acl -Path $_.Path
$acl.SetSecurityDescriptorSddlForm($_.Sddl)
Set-Acl -Path $_.Path -AclObject $acl
}
E.g: “Output File” -> “D:\Export\Export.csv”
Vyapin is a developer of Security tools for Windows Enterprise and Cloud. If you are looking for Security Audit and Management tools for your Windows File Servers, you may download and evaluate the free trial version of the following products: