Ever wondered about the activities mentioned below happened in your Office 365 environment?
Ever wondered about the activities mentioned below happened in your Office 365 environment?
- Who had deleted or checked out a document which belongs to you?
- Who had assigned the license to a user?
- Who had added or removed members from group?
- Who had downloaded some sensitive documents recently?
Just view your Office 365 Audit logs available in the Office 365 Security and compliance center which helps you in finding out what users in your organization have been doing.
Office 365 stores a voluminous amount of information in its audit logs with events available for almost every activity that happens in Office 365. There are various categories or types of events and each category has a number of events pertaining to activities that happen in that category. The Audit log search feature in allows you to search for specific activities that happened in the last 90 days.
So, what are the event types available in the Audit logs?
- User activity in Exchange Online, SharePoint Online and OneDrive for Business
- Admin activity in Exchange Online, SharePoint Online and Azure Active Directory
- User and Admin activity in Sway
Getting started
Before you start using the audit log search, an admin must enable the auditing option in the Security and Compliance center. To enable this, go to Audit Log Search page in Security and Compliance center -> Search & Investigation and click on Start recording user and admin activity. This is a one-time action to perform.
If the link is not available it means that auditing is already enabled in your tenant. After enabling, a message will be shown that the audit log is being prepared and that you can run a search in a couple of hours after the preparation is complete.
Permissions required
To perform the audit log search you must be assigned View-Only Audit Logs or Audit Logs role in Exchange role groups. By default, these roles are available with the Organization Management role group and Compliance management role group. If you do want to assign these role groups to the user, you can always create a custom role group with either of these roles and add users to them.
How to perform an audit log search?
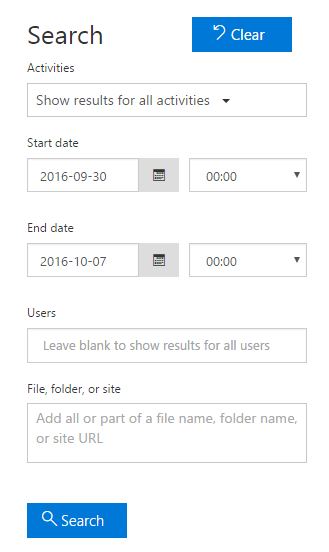
Once you navigate to audit log search page, the search page will appear as shown below. Let’s see the various search options available in that page.
Activities:
Once you click the drop-down field of activities, you can see all the event categories and events available for performing search operation. By default, if you click on the search button, you will see event traces for all the activities available. You can also see event details for specific events using the activities drop-down.
Start date and End date:
By default, only the last 7 days are selected for performing the search operation. You can change date to view the events occurred in the selected date range. Note that the maximum date range you can specify for performing the search operation is only 90 days.
Users:
You can select users for whom you want to see the event details. The events performed by the selected users will be displayed in the search results. If you want to view results for all the users, leave this field as blank.
File, folder or site:
Specify the name of a file / folder / site URL to view the activities performed on the specified file or folder. If you want to view results for all the folders and files, leave this field as blank.
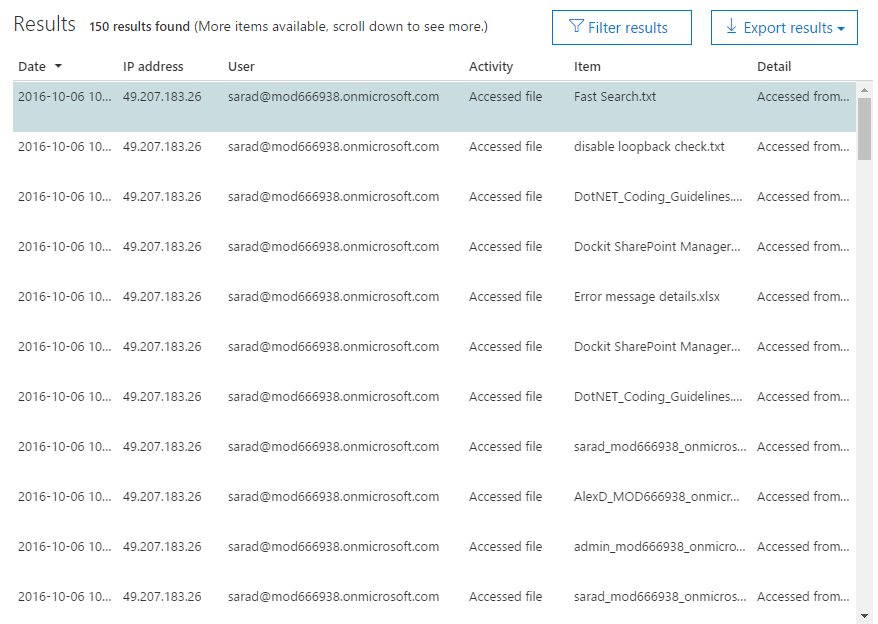
Once you click on search, after entering the required details, the audit event results will be displayed based on the search criteria as shown below.
By default, only 1000 results will be shown in the search results. If more than 1000 results are available, the newest 1000 events will be shown.
Export audit logs
There are two exports options available to export the audit data. You can use the Save loaded results option to export the data which you see in the search results. Note that if there are more than 1000 results available, only the newest 1000 events will be exported using this option.
If you want to export all the results, you can use another option called Download all results. Using this option you can export up to 50,000 events. If the event results exceed 50,000 results, you have to modify your search criteria or perform a granular search for exporting all the data. Export operation may take some time depending on the volume of data returned in the results.
Limitations of audit Log search:
- Maximum date range you can specify for performing the search is only 90 days.
- Only the newest 1000 events can be viewed in the search results page.
- Both the search results page and the exported file will show the raw event detail data which is not user-friendly and makes it cumbersome for filtering and auditing data.
Conclusion
Office 365 Audit logs are very important for Security in Office 365. These audit logs can also be accessed and events can be extracted programmatically using the Office 365 Management Activity APIs and also using PowerShell. While the Search feature available Office 365 allows you to track events in an adhoc manner for the last 90 days, you will certainly need third party tools if you need to store and retrieve long term activity data for Security and Compliance needs of your organization.
Vyapin Microsoft 365 Reports module now has a separate feature Audit and Compliance reports to enable organizations to report on various event activities and archive them for long term storage.
Download free trial version of Microsoft 365 Reports Now!