“Companies spend millions of dollars on firewalls, encryption, and secure access devices and its money wasted because none of these measures address the weakest link in the security chain: the people who use, administer, operate and account for computer systems that contain protected information…”
– Kevin Mitnick,
Computer Security Consultant, Author, Hacker
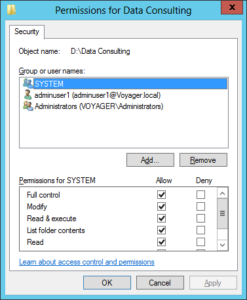
A security professional offers protection for an organization’s computers, networks, and data by determining who gets access to what and maintaining an overall state of order. This is the critical link in the security chain and the better equipped they are, the better managed an organization’s strategic electronic assets. One secret weapon that security and system pros use to get the job done is Vyapin’s NTFS Security Management Suite. NTFS Security Management Suite brings all the power and muscle needed to address the challenge of managing and maintaining a secure environment. The suite couples access control and auditing management with automated data collection and reporting, and backs that all up with Vyapin’s highly-responsive support team.
Access
The attention grabbing security headlines these days focus on sophisticated phishing attacks and cyber terrorism. Interestingly, a poll conducted by the British Standards Institution found that 37% of respondents identified employees as the biggest information security threat. It can be a delicate balance to manage providing access, enabling productivity, and securing an organization.
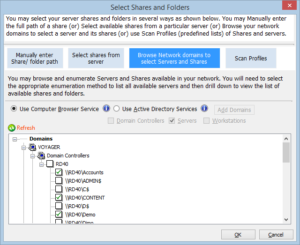
One way to protect organizational assets is to make sure that the right people have access to the right information only for the period of time they require it. From a practical point of view, this is easier said than done. The reality of the situation is that systems and security professionals in mid and large size organizations can be tasked with managing large networks with thousands of servers that have huge storage capacities. At the same time, the dynamic nature of business today sees employees or contractors regularly joining and leaving an organization, bringing in devices of their own choosing, and frequently changing roles and responsibilities. Throw in the additional complexities of regulatory requirements like HIPAA and SOX and managing access can seem all the more daunting.
By way of example, a healthcare company with 1300 servers was feeling the pinch. They needed to manage all of their domain file shares and identify which had open permissions (those where the “Everyone”, “Domain Users”, or “Authenticated Users” groups had access) in order to further inspect those shares to see if access was properly controlled. The organization had limited time and limited resources to spend on this effort and so it turned its attention to finding tools that could be leveraged. The search led them to Vyapin and NTFS Security Auditor, a powerful, flexible NTFS permissions auditing and reporting tool.
NTFS Security Auditor provided this client with:
- The features and control needed to efficiently gather information;
- An ability to generate essential reports;
- A solution that did not impact network performance or employee productivity.
Automation
Even the most dedicated systems professionals do not spend 24 hours on the job. Nor would their employers expect them to as it would eventually lead to burnout and ineffectiveness. IT departments are acutely aware that there is not enough time in a day to get everything done. Automation is one way to better manage the clock.
A large agriculture and food manufacturing company faced the task of automating an audit of more than 1000 servers, each with a capacity of up to several terabytes of storage and a large number of associated Access Control Lists (ACLs). The sheer size of this environment meant that it would take days to run a complete audit. As such, the organization needed an automated tool that would allow them to streamline the process as much as possible. The tool would need to provide the ability to set the right level of granularity for data to be gathered and most importantly, would need to gracefully handle any error conditions that might arise by highlighting those to administrators without impeding the completion of the audit.
NTFS Security Auditor was the perfect fit for this large scale deployment:
- It is optimized for fast performance resulting in efficient data collection;
- The software’s flexible reporting options can be used to reduce the volume of data scanned.
In this particular case, the reporting was used to highlight certain types of ACLs to prompt the organization to carry out further investigation and analysis.
Managing with Agility
Once an organization’s current computing environment is understood and adjustments have been made to align to policy requirements, attention turns to making sure the desired state is maintained. This includes being able to quickly adjust to unforeseen but typical changes that arise in business environments due to the introduction of things like new industry compliance requirements, risk management strategies, or changing business priorities. Being able to respond to these changes with agility is the key to success here.
An example of agility at work can be seen in one particular IT Services firm where a business change introduced the requirement to revoke write permissions for all users on folders and files in the organization’s environment. Due to the firm’s large directory structure a purely manual approach would have been prohibitively time consuming and error prone. To meet the challenge, the firm implemented a product from Vyapin’s Security Management Suite called NTFS Security Manager. This tool enabled the organization to quickly and easily revoke the desired permissions and maintain the integrity of their environment.
Support
“I finally got everything tested and it looks good! It will give us the ability to deploy on a large scale. I just wanted to say thank you again for such quick response and turn-around.”
“Many thanks again for your hard work and assistance. This is a great product and we are so close to making it work in our large enterprise. I hope you share my excitement with what we are about to achieve…”
Vyapin Customers experiences
Strapped for time and constantly attuned to risks and surveying threats to the organizations, IT Systems and Security Professionals need to know that someone has their backs. Selecting software that makes auditing and managing security easier helps but everyone need back up once in a while. Vyapin’s customers know they have talented, committed experts ready to support them when the going gets tough. From the first evaluation to the final rollout, the Vyapin support team is consistently recognized by its customers for its responsiveness, flexibility, and for delivering exactly as promised.
Conclusion
Security and systems management professionals use communication and awareness of the rules to manage demanding situations with grace and finesse. They are the critical link in protecting the most valued assets of their employers. Whether it is determining access, maintaining a positive situation, handling exceptions, or responding to changes quickly, it never hurts to have a little muscle, power, and edge. Working with Vyapin and deploying NTFS Security Suite to protect strategic assets gives organizations that edge.
Vyapin builds intelligent, cost-effective Systems Management solutions that bridge the gaps in Data, Information and Knowledge that exist across the enterprise – its Systems, processes and people. Vyapin’s objective is to offer world-class products and solutions that address the demanding needs of Systems Management for the evolving Enterprise. The company’s core competence is the product of a continuous learning process driven by technology expertise, customer satisfaction and evolving market needs.